

Yeah, I’m an avid mac/i/iPadOS user, and that was a bad choice. And it’s sad, because it feels like a choice made just to have something to reveal at WWDC. I’d respect them a whole lot more with optimizations, performance improvements, and developer enhancements. I was good with 18, not to mention some elements from the older designs.







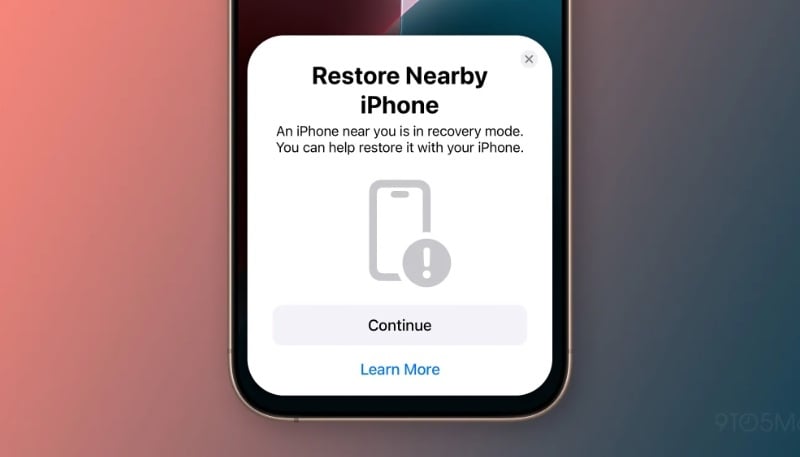
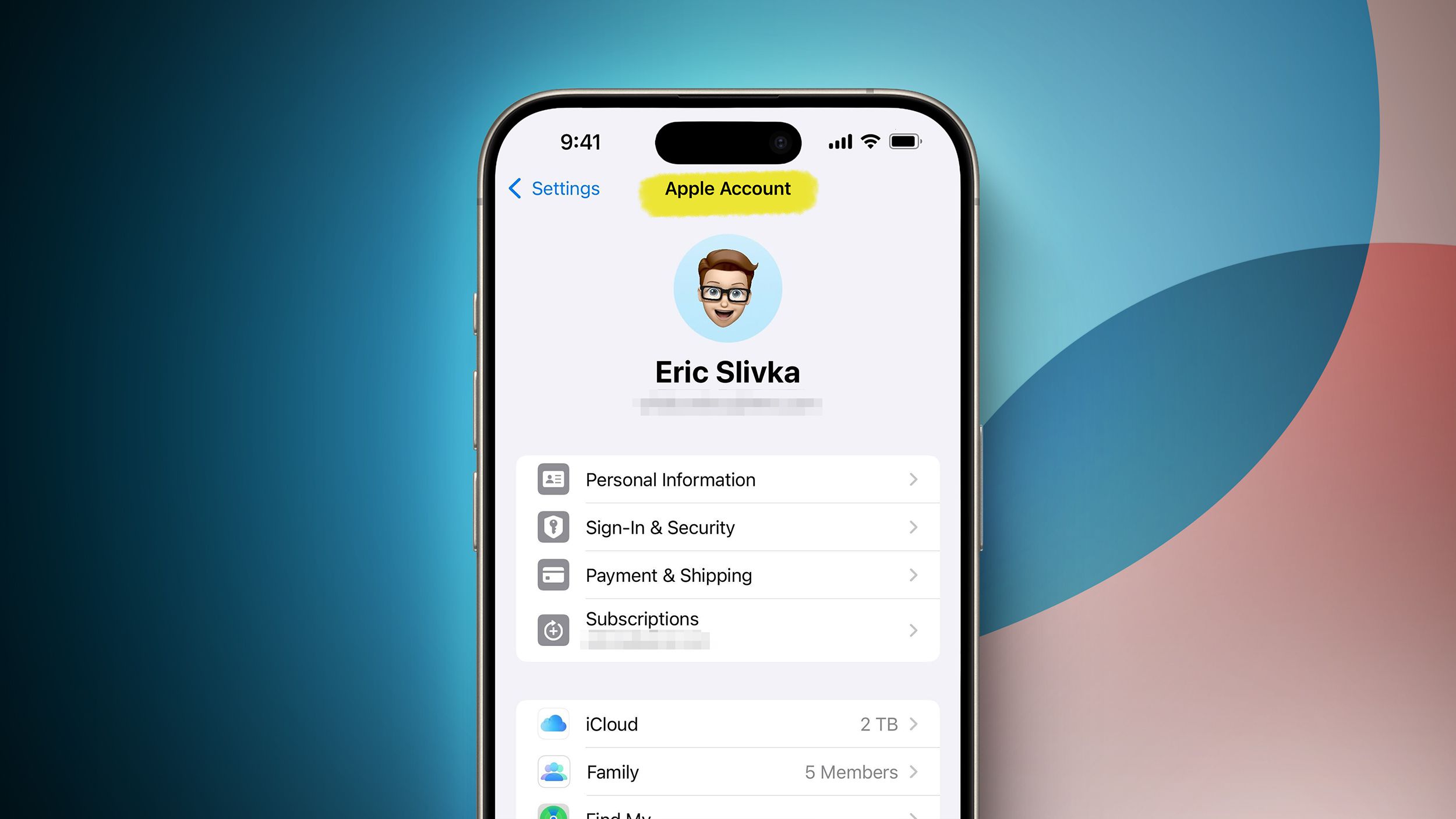


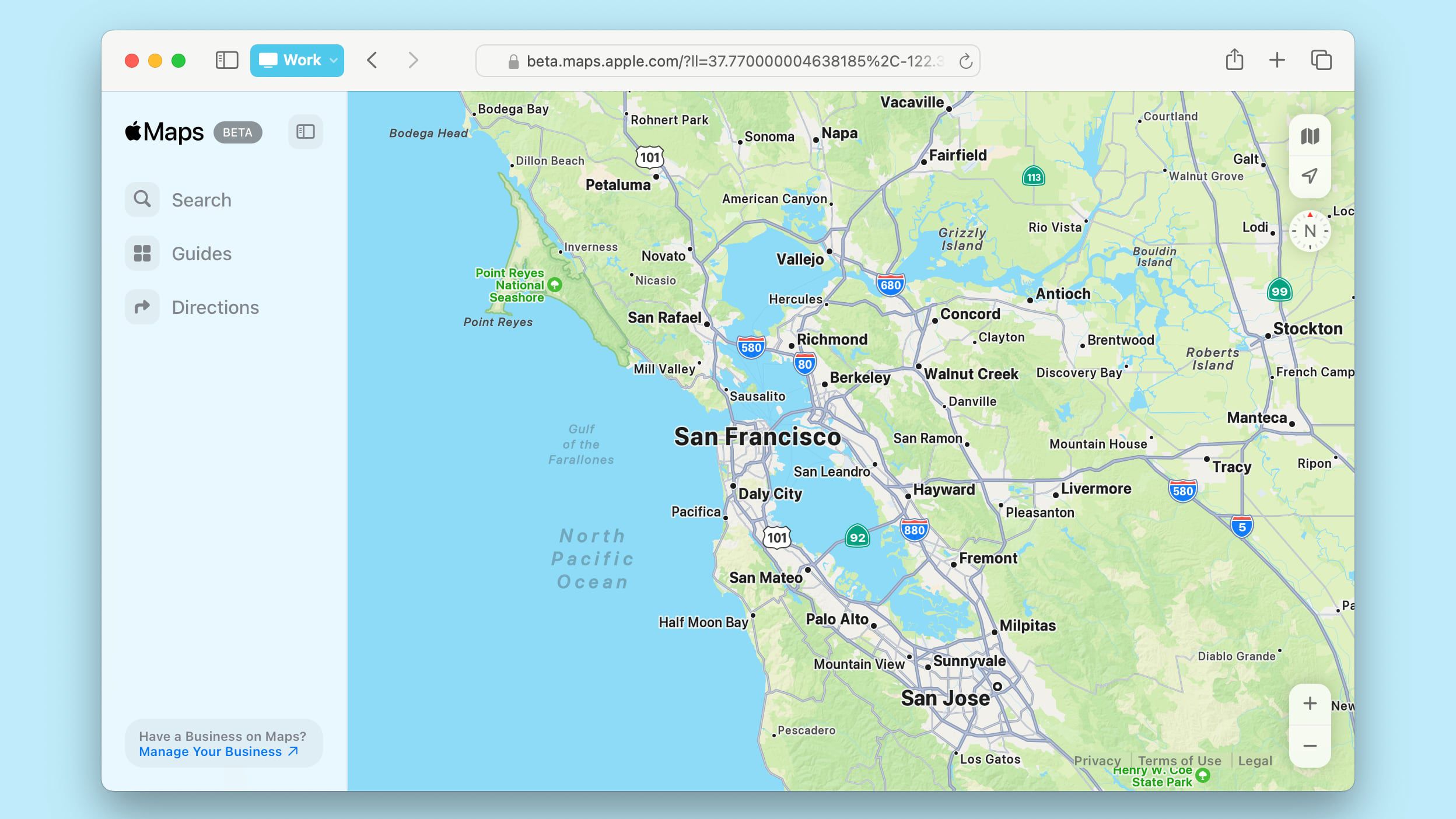

schwing.